Take a poll of IT and Security professionals at defense contractors, they will tell you that positioning the company to obtain Cybersecurity Maturity Model Certification (CMMC) is near to or at the top of their list of priorities. This if for good reason. The DoD and other Federal agencies have made it clear that managing Controlled Unclassified Information (CUI) in a safe and responsible manner is required to do business with the government. Several years ago the Fed sent a signal that we all needed to get serious about protecting CUI, CMMC is the evolution of that call to action.
Why and when was the CMMC created?
Prior to 2008 the U.S. Government had more than 100 designations for unclassified information. Terms like “Sensitive But Unclassified” (SBU), Sensitive Security Information (SSI), For Official Use Only (FOUO) are some examples that you may have seen. President George W. Bush directed the consolidation of unclassified information reference to the single use of CUI, and subsequently President Barrack Obama through Executive Order (EO) 13556 sought to carve out guidelines that would create uniform use of the information control standard across all Federal Agencies. EO 13556 defines CUI as government created or owned information “that requires safeguarding or dissemination controls pursuant to and consistent with law, regulations, and Government-wide policies”. To understand what should be classified as CUI, you can visit the CUI Registry. The Registry lists the 84 CUI Categories and provides a description with category marking requirements.
Even though CUI isn’t considered classified the Information Security Oversight Office (ISOO) warns “the loss or improper safeguarding of CUI could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. The loss or improper safeguarding of CUI has a direct impact on national security”. They point to the Office of Personnel Management (OPM) data breach announced in June of 2015 as a costly example of the damage incurred when CUI is not properly protected. In this breach personnel files of 4.2 million former and current government employees were penetrated by bad actors. The vulnerability exploit jeopardized national security and burdened tax payers with tremendous costs to mitigate the security disaster (it cost the government $350 million to notify and protect those impacted by the breach).

In an effort to strengthen national security related to CUI protection, Defense Federal Acquisition Regulation Supplement (DFARS) clause 252.204-7012 was published in the Federal Register. Contractors were given until December 31, 2017 to implement security requirements detailed in NIST SP 800-171 (800-171). The SP 800-171 publication details in 100+ pages recommendations and standards for protecting CUI in nonfederal systems. Presently, Defense Contractors are required to self-assess and report their cyber security readiness against the NIST SP 800-171. However, in August 2018 MITRE released a report for the DoD recommending additional steps be taken to create standards for security. They noted “Medium and small-sized suppliers frequently complain that they need consistency and coordination in establishing security credentials”, and warned that many contractors are likely falling short of their NIST SP 800-171 attestation. The Office of the Under Secretary of Defense Acquisition and Sustainment (OUSD A&S) responded to data security concerns by announcing in 2019 that they will require all defense contractors to obtain Cybersecurity Maturity Model Certification (CMMC). This made clear their intention to mandate additional requirements to obtain concrete assurance that DoD contractors and subcontractors will protect sensitive unclassified information.
CMMC 1.0
Cybersecurity Maturity Model Certification (CMMC) 1.0 sent shockwaves through the defense industrial base (DIB). The DoD made it clear that security has become a primary metric used to make acquisition decisions. All future RFP’s will include a CMMC level requirement that must be met to be awarded a contract.
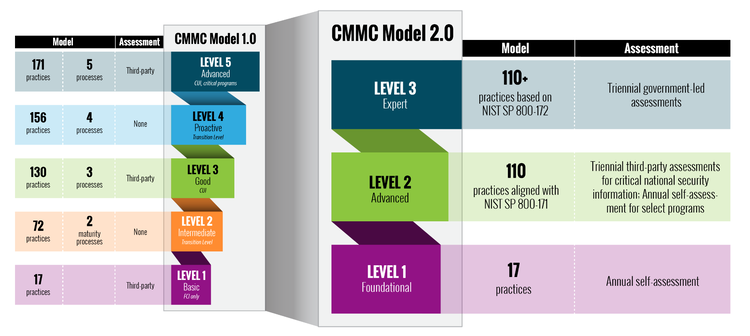
CMMC primarily leans on the standards put forth in NIST SP 800-171 to identify a contractors security certification level. The intention was to put an end to security compliance attestation and required a CMMC third party assessment organization (C3PAO) to verify the CMMC level. The DoD initially had an aggressive timeline to implement CMMC; they expected by Q3 2021 20-100 contracts will require CMMC certification and 1,500 top DIB contractors would be certified. But the DIB was not willing to move that fast. Industry had many questions and concerns regarding CMMC 1.0. The DoD reported 850 public comments in response to the interim rule and decided revisions were required to implement CMMC. In November 2021, the DoD announced CMMC 2.0.
What changes were made in CMMC 2.0?
After receiving feedback from the DIB, the DoD determined they need to find ways to reduce costs to obtain CMMC, improve confidence in the CMMC assessment process, and the requirements needed to be clarified and aligned with commonly accepted standards. OUSD A&S states CMMC 2.0 brings the following key changes:
- Streamlines CMMC from 5 to 3 compliance levels.
- Aligned with widely accepted (NIST) cybersecurity standards.
- Reduced assessment costs, allows all companies at Level 1 (Foundational), and a subset of companies at Level 2 (Advanced) to demonstrate compliance through self-assessments.
- Increased oversight of professional and ethical standards of C3PAO
- Allows companies, under certain limited circumstances, to make Plans of Action & Milestones (POA&Ms) to achieve certification
- Allows waivers to CMMC requirements under certain limited circumstances
What does CMMC 2.0 mean for government contractors?
The publication of CMMC 2.0 materials reveals the Governments intention to include security requirements in future contracts. While there are no existing contractual requirements to comply with CMMC 2.0, the rulemaking process is underway. Contractors can expect changes to the DFARS and Code of Federal Regulations (C.F.R.). While the DoD intends to suspend the CMMC pilot efforts in existing solicitations, Contractors will be obligated to meet the CMMC requirements once the rulemaking process is completed. The OUSD A&S estimates it will take 9 to 24 months to incorporate the CMMC requirements into the DFARS and CFR.
CMMC may not go live in contracts until 2022 or even 2023, but Contractors cannot afford to delay implementing the security requirements necessary to obtain a CMMC level. Any contractor that handles CUI will need to at least achieve CMMC level 2. This means implementing all 110 controls in NIST SP 800-171. The DoD’s position is that under DFARS 7012 Contractors should already have NIST SP 800-171 controls in place. If you are compliant on your existing contracts, no additional runway is need to obtain CMMC level 2.
Anyone that has submitted their 800-171 assessment to the Supplier Performance Risk System (SPRS) will say it’s no picnic. Factor in additional time to enter the data and obtain your results. Some contractors may be tempted to relax their progress to obtain CMMC level 2 because now POA&M’s are available to bridge the gap between their current assessment score and the CMMC level required to obtain a contract. My recommendation is to not take the bait. Approved POA&M’s will likely stipulate that the contractor will have a short window to cure inadequate security controls, and thus should only be requested when the organization has high confidence they can rapidly implement security provisions and pass 3rd party assessment. I’ve heard C3PAO’s estimate that the assessment process will take roughly two weeks to complete, longer if insufficiencies need to be addressed.

Organizations should understand that CMMC is expected to eventually impact practically all Federal Contractors. Also, those that do business with civilian organizations that leverage GSA contracts will be impacted. The draft of Polaris, a new GSA government IT services contract, includes language suggesting contractors will need to comply with CMMC in the future. GSA officials are reported to state in the RFP “While CMMC is currently a DOD requirement, it may also have utility as a baseline for civilian acquisitions. It’s vital that contractors wishing to do business on Polaris monitor, prepare for and participate in acquiring CMMC certification”.
There is some great news for those ready for CMMC Level 2. Multiple sources reported that CMMC policy makers would like to implement incentives for those who obtain Level 2 certification early. They recommend permitting Level 2 holders “garner a higher profit margin” and “will assess people’s network security as part of a source selection evaluation”. Getting CMMC sorted out now could help differentiate you even before the CMMC requirement is officially implemented.
How does CMMC impact government property managers?
Management of CUI is a daily job for those that control government property. Skeptics can take a look at CUI categories Controlled Technical Information, DoD Critical Infrastructure Security Information, and General Procurement and Acquisition. These are considered “buckets” for Government property and contract data. It makes sense! Knowledge of who has government assets and what they are doing with them should be information that is controlled.

If your IT and Security team have not already started discussions with you around CMMC, they will. The systems used to manage government property data will be included in the CMMC assessment. The system (and if hosted, the supporting vendor) will need to have NIST SP 800-171 controls in place for your organization to obtain CMMC Level 2. This means organizations that have been putting off transitioning to a purpose built government property system will need to make the switch prior to CMMC going into effect. Basic tools like spreadsheets, Access databases, and other systems not built specifically for government property compliance have numerous vulnerabilities that make them unable to support all 110 NIST SP 800-171 controls. We encourage you and your IT Security team to access the FAR/DFARS Cyber Security Questionnaire (include link to questionnaire), it will help you assess how your existing government property management tool stacks up to the SP 800-171 controls. Here are some examples where basic tools fall short:
- Limit system access to authorized users, processes acting on behalf of authorized users, and devices (including other systems).
- Limit system access to the types of transactions and functions that authorized users are permitted to execute.
- Prevent non-privileged users from executing privileged functions and capture the execution of such functions in audit logs.
- Encrypt CUI on mobile devices and mobile computing platforms
- Ensure that the actions of individual system users can be uniquely traced to those users so they can be held accountable for their actions.
- Provide a system capability that compares and synchronizes internal system clocks with an authoritative source to generate time stamps for audit records.
- Use multifactor authentication for local and network access to privileged accounts and for network access to non-privileged accounts.
- Employ FIPS-validated cryptography when used to protect the confidentiality of CUI.
Once CMMC starts showing up in DoD contracts, organizations should expect a limited grace period to have a compliant government property system in place. It is likely your existing DoD contracts have DFARS clause 252.204-7012. It was published in 2017 and requires organizations to already have a system that can protect CUI using all SP 800-171 controls.
What do government contractors need to look for in a government property system (and vendor) to support CMMC?
As with most government contractor systems, property management is being required to implement modern software systems for organizations to maintain a competitive advantage. We have noted a lot of changes to the government property reporting systems (e.g. PIEE, GFP module), CMMC is yet another push toward partnering with an experienced company that provides a purpose built modern government property system.
There are key attributes that help distinguish a suitable vendor from those that are not a good fit. One clear red flag is if they are unfamiliar with the CMMC requirement. This one may seem obvious, but I have observed that many contractors are not screening for vendors with CMMC Level 2 compliance in their roadmap. Check your existing software vendors website for mention of compliance with CMMC. Better yet, ask them to complete this FAR/DFARS Cyber Security Questionnaire (link to file) to get their NIST SP 800-171 attestation in writing. If they check “Yes” on 110 out of 110 of the controls, then they are ready for CMMC Level 2. To be compliant, the operations staff of qualified vendors will also have completed the Defense Counterintelligence and Security Agency (DCSA) CUI training and certification test. This is mandatory training for anyone that handles CUI.

If you choose a system that is vendor hosted, ensure it complies with DFARS 252.204-7012 (b)(2)(ii)(D): “If the Contractor intends to use an external cloud service provider to store, process, or transmit any covered defense information in performance of this contract, the Contractor shall require and ensure that the cloud service provider meets security requirements equivalent to those established by the Government for the Federal Risk and Authorization Management Program (FedRAMP) Moderate baseline (https://www.fedramp.gov/resources/documents/) and that the cloud service provider complies with requirements in paragraphs (c) through (g) of this clause for cyber incident reporting, malicious software, media preservation and protection, access to additional information and equipment necessary for forensic analysis, and cyber incident damage assessment.”. Confirm with the vendor that they are hosting their solution on FedRAMP compliant servers, something like Amazon Web Service GovCloud.
Another way to assess whether a system is capable of helping you meet CMMC compliance is by evaluating the Role-Based-Access-Control (RBAC) functionality. The systems RBAC should be customizable by your team. Configurable RBAC permits you to tailor permission controls for users in the system that are inline with your procedures. You should be able to limit access to assets by groups like Contract, Project, Location, and Department. You also need to be able to hide data fields, reports, and workflows from certain users. Any transaction completed by a user should be displayed in history logs and reports. The data should show the user that made the change, when it was made, what the data was prior and what it was changed to.
CMMC marks a clear change to how the Federal government will hold contractors accountable to protecting government property data. We expect that contractors will start demanding the same level of accountability and capability from their government property solution providers. eQuip is ready to help.

